Employees and customers alike beware! Email impersonation is on the rise – and hackers are constantly finding new ways to trick their targets, like in the scenario below.
The Scenario
John Baker was nearing the close on the sale of his home. He had one more task to complete before his signing appointment the next day – initiate a wire transfer for his closing costs. He was in line at the bank when he received an unexpected email from his title agent, Rob Lee:
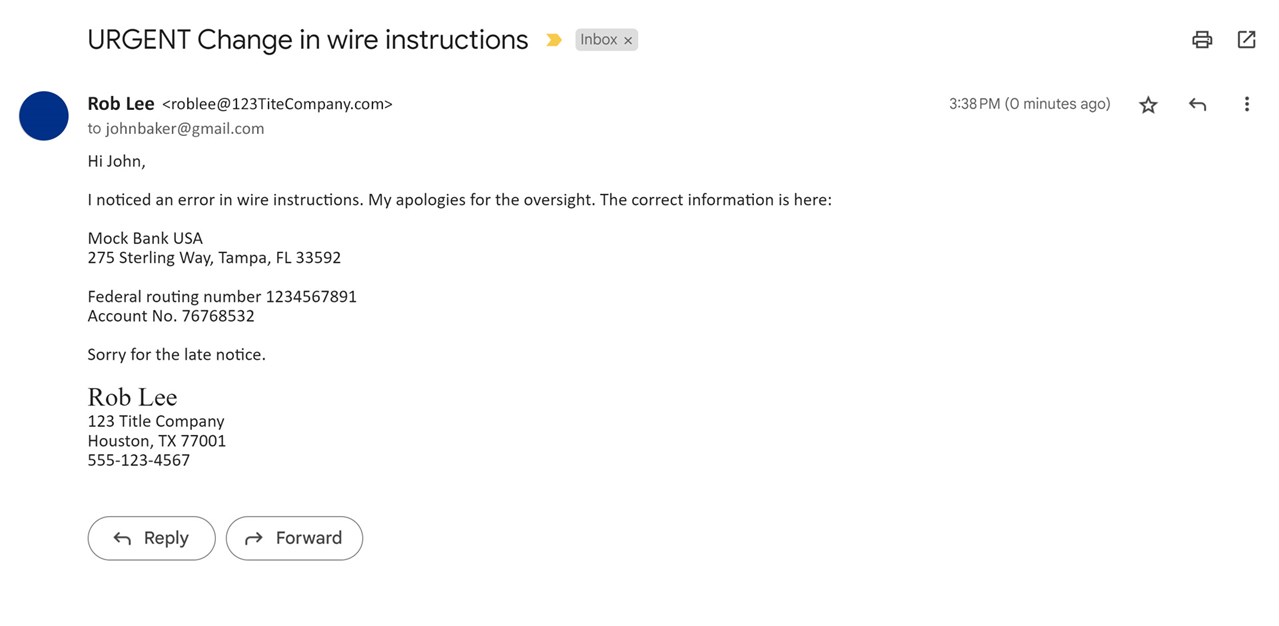
Although a bit frustrated by the mistake, John felt fortunate that he saw the email before he reached the teller’s window and was able to update the bank account before wiring his closing funds.
The next morning, John walked into 123 Title Company where Rob Lee worked, excited for his signing appointment. As soon as Rob walked into the lobby to greet John, he said, “We haven’t received your wire. Did you send it?” John was baffled and replied, “I don’t know why not. I sent it yesterday with the updated information you sent me.” Rob’s facial expression immediately turned from confusion to fear. “I didn’t send you an email yesterday,” he stated. John replied “Yes, you did,” as he reached for his phone. He pulled up the email and handed the phone over to Rob. Rob looked up and said, “This isn’t good. I didn’t send this email.”
After discussing the incident, it was apparent that John and Rob were victims of a business email compromise (BEC) impersonation attack – a type of phishing attack where a malicious actor creates an email address that looks like it came from a legitimate business and impersonates an employee to fool consumers into diverting funds into a bank account owned by the fraudster. In this situation, the urgent request for change in wire instructions came from the email address roblee@123TiteCompany.com, but Rob Lee’s email address is roblee@123TitleCompany.com. The fraudster’s email was missing the “l” in “Title.” The phone number in the message also didn’t belong to Rob. Luckily, Rob promptly followed company wire fraud procedures and was able to recover John’s funds.
A Growing Tactic
While the names and details in the scenario above are for illustrative purposes, they are based on real events. Unfortunately, this scenario is only one of several types of email impersonation tactics seen in the real estate and title industries. Fraudsters aren’t just impersonating title professionals, but all parties to a real estate transaction, even the buyer and seller. If you think email impersonation fraud is limited to residential transactions, think again! The large sums of money exchanged during a commercial transaction make them a prime target as well.
How to Outsmart the Fraudsters
Always be wary of unexpected communications that urge you to take immediate action – even if they appear to come from someone you know. Cybercriminals are super sneaky, so it’s up to us to stay one step ahead by following these best practices:
• Educate yourself on emerging schemes. Click here to learn more from the Federal Bureau of Investigation (FBI) about common scams and crimes, and how to prevent them.
• Practice good cyber hygiene. To help mitigate cybersecurity risks, implement good cyber hygiene habits like using strong and complex passwords, protect email accounts with multi-factor authentication (MFA) and using a virtual private network (VPN) when connecting to the public wi-fi. For more cyber hygiene tips, click here.
• Learn to recognize red flags. While phishing schemes are constantly evolving, most attempts include urgent requests and unexpected emails. Last-minute changes in wire instructions, like the one that John received in the story, are another telltale sign of fraud.
• Stay vigilant. Cybercriminals know we’re all multitasking, and they’re hoping we’re too busy to stop and question requests that appear to come from someone we know. Don’t fall for it!
• Never use contact information in an unexpected communication – even if you recognize the sender or have done business with them in the past. You can never really be sure who is on the other end of that communication, so it’s best to disengage and go straight to the source.
• Always call a TRUSTED phone number to verify the request BEFORE acting on it. If John would have called Rob using a trusted phone number to verify the change in wire instructions, he would have avoided exposing himself to fraud and potential loss.
Pro Tip: Customers should reference the list of phone numbers provided by their title professional.
Don’t worry about looking silly or offending anyone by double checking unexpected requests; true professionals will understand and appreciate the effort you put into verifying the request. If the company is unaware that someone is impersonating a current or former employee, reporting it gives them the opportunity to warn others and take steps to mitigate the fraud. (Which kind of makes you a hero, too!)
To learn more about common cybersecurity threats to your business, click here. Real estate customers can also check out these tips for preventing wire fraud, which often starts with business email compromise and email impersonation.
